








Thanks to the SpearID FIDO2 key, hijacking the user account is practically impossible. The security key replaces all passwords, protects account information from fishing, data breaches, malware and hacking, because the physical key cannot be stolen over the network. The security of FIDO technology is better than any other two-factor authentication.




One SpearID FIDO2 identification key protects access to hundreds of applications and services. One and the same SpearID FIDO2 key can be connected to all services that support FIDO or other two-part identification. To be sure, the same user account can also be protected with several different FIDO-compatible keys.




Implementing the SpearID FIDO2 security key is quick and easy: with a couple of button presses, you can protect your account in less than a minute. The SpearID FIDO2 key works like your own home key - only you know which service and account the key goes to.



More and more services support two-part identification, e.g. by e-mail, text message or mobile application. Since the two-part authentication event cannot be reliably connected to the user's web browser, an attacker can hijack the account remotely. Only a physical security key can prevent an account from being hijacked by a sophisticated attack.



All identification methods based on passwords are vulnerable to data breaches, and even the longest password cannot protect the account from being hijacked. An attacker uses several different methods to circumvent or break password protection. It is also possible to bypass the two-part identification with current technologies.



Security is not the default on the Internet. Millions of passwords from popular services are leaked every day. Hijacking user accounts is easy, because the use of passwords alone is no longer safe. While the protection of popular online services improves, the tools of attackers develop even more.



More and more services support two-part identification, e.g. by e-mail, text message or mobile application. Since the two-part authentication event cannot be reliably connected to the user's web browser, an attacker can hijack the account remotely. Only a physical security key can prevent an account from being hijacked by a sophisticated attack.



All identification methods based on passwords are vulnerable to data breaches, and even the longest password cannot protect the account from being hijacked. An attacker uses several different methods to circumvent or break password protection. It is also possible to bypass the two-part identification with current technologies.



Security is not the default on the Internet. Millions of passwords from popular services are leaked every day. Hijacking user accounts is easy, because the use of passwords alone is no longer safe. While the protection of popular online services improves, the tools of attackers develop even more.
There are only three simple steps to deploying a SpearID FIDO2 authentication key. Best of all - all these steps are very similar for all supported services (eg Google services).
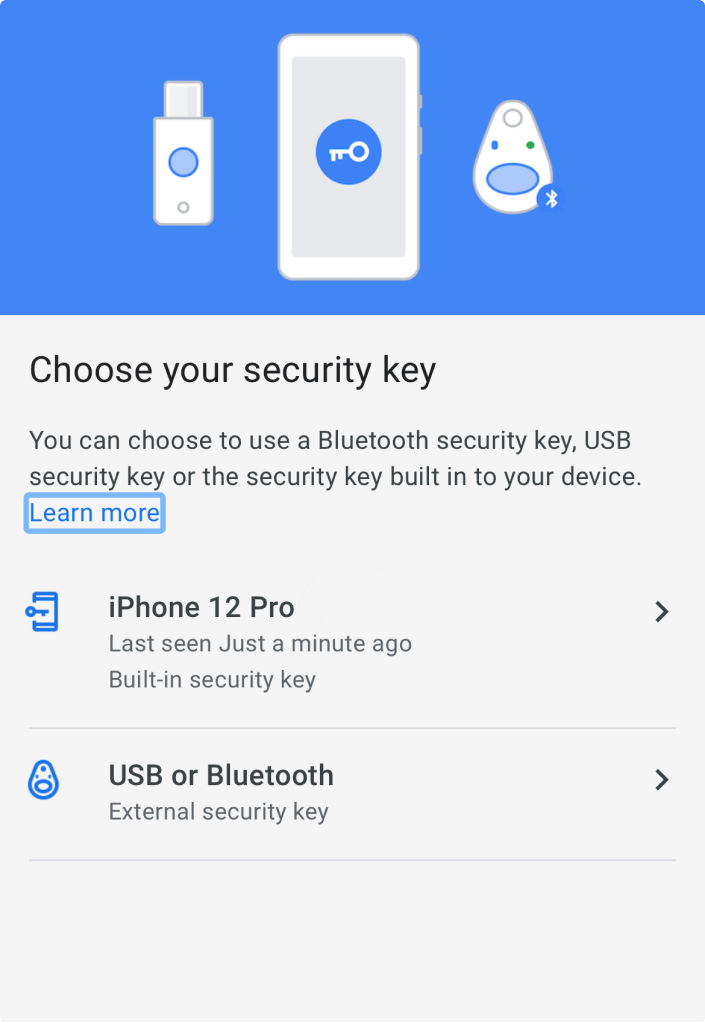

1. Registration starts by adding the SpearID FIDO2 security key to your account. In the user account settings of the supported online service, there is a point "two-step authentication" where you can add a "Security Key" security key (or security key).
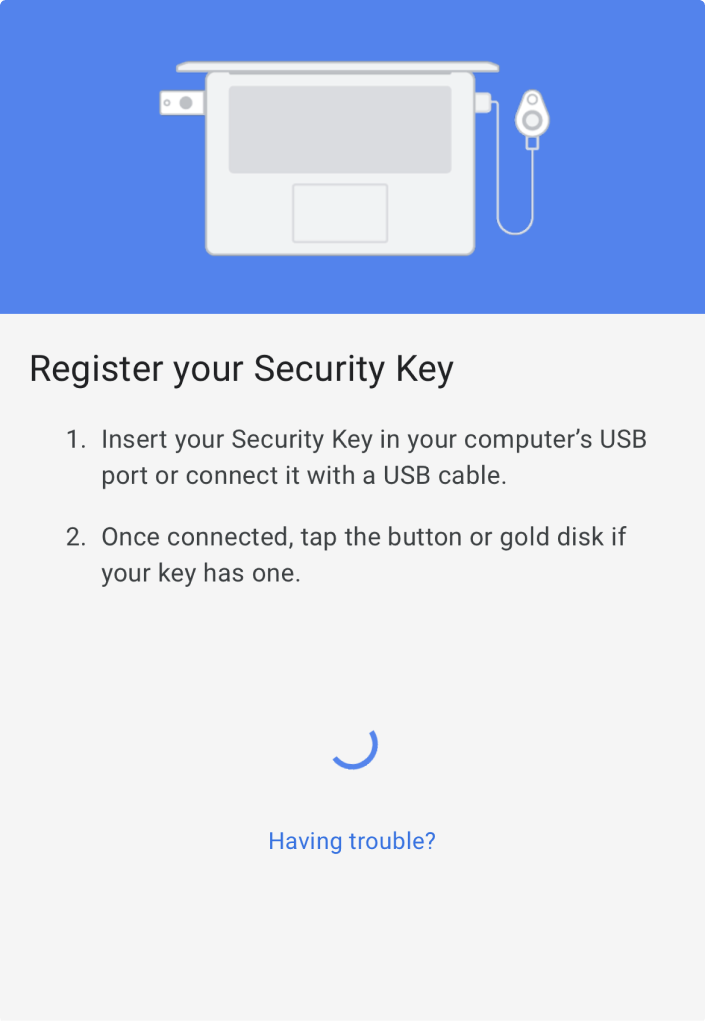

2. Registration takes place by connecting the SpearID FIDO2 key to the computer's USB port and pressing the small key button on the stick. For NFC proximity reading, the key must be pressed against the back of the smartphone with the USB reading surface folded open (about 3s).
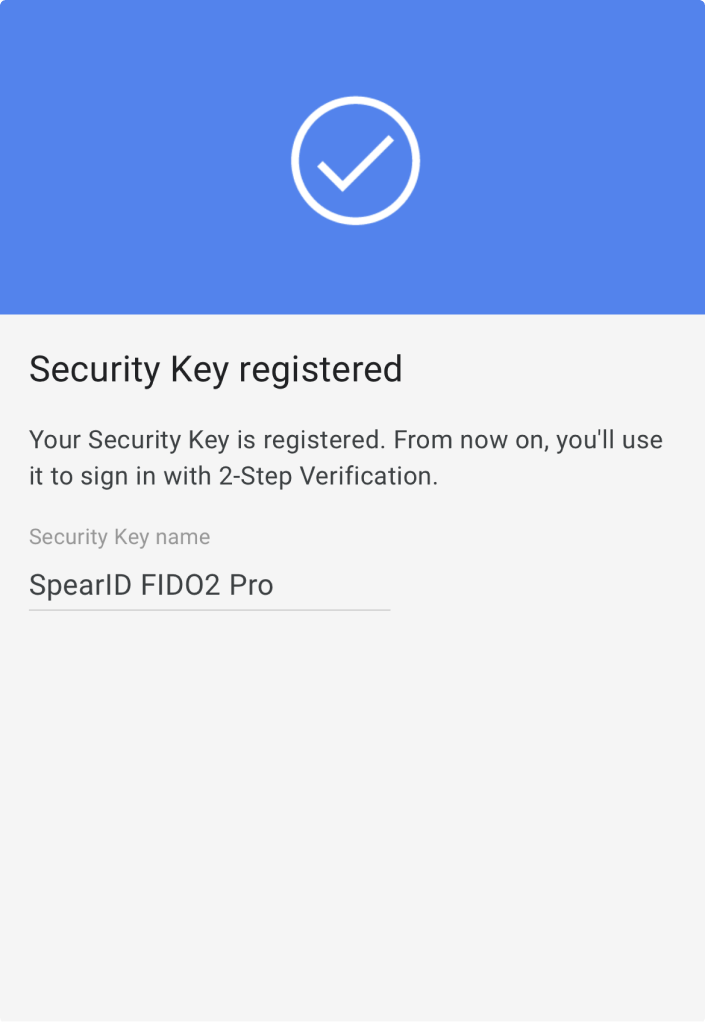

3. After successful registration, SpearID FIDO2 keys can be assigned a service-specific name to distinguish them from other security keys. Several services also offer the option of adding a PIN to the security key. Note! You should add a PIN code to the FIDO key, as some services require it to work correctly


SpearID FIDO2 is a certified identification key according to the FIDO standard. The number of supported online services and applications is growing all the time. In addition to FIDO-supported services, the SpearID FIDO2 key also supports other general two-part identification services. See the list of supported services below.




- Make sure that the security key is folded open and you touch the top of the phone with it according to the instructions in accordance with. - Make sure that the service you are using is ready to establish an NFC connection - The service may require that you have registered the PIN code security key in connection with.
Having two FIDO keys is recommended. You can register more than one key for one user, so if one key fails, you can use the other.
- Yes. If your device has a Bluetooth connection and the service you use supports the key's Bluetooth feature, you can take advantage of this when logging in. - MacOS does not currently support the Bluetooth feature of FIDO2 security keys, so here devices, you cannot take advantage of the Bluetooth capability.
The key can only be used for identification on the phone, but it must be taken to use and register on the computer.

